Billions Of Gmail Accounts Threatened By Stealthy ‘No-Reply’ Hack
What You Can Do to Stay Safe from Hyper-Realistic Phishing
Phishing scams aren’t what they used to be. Gone are the clunky layouts, the spelling mistakes, and the fake email addresses. These days, some scams are so sophisticated that even seasoned tech users have to do a double-take.
One recent example, analyzed by Ethereum Name Service founder Nick Johnson, shows how convincing a phishing attempt can be when it’s cleverly disguised to look like an official message from Google.
Last month, Johnson shared a thread on Twitter dissecting a particularly sneaky phishing email he received. At first glance, it looked completely legitimate.
It even passed technical checks designed to detect fraud.
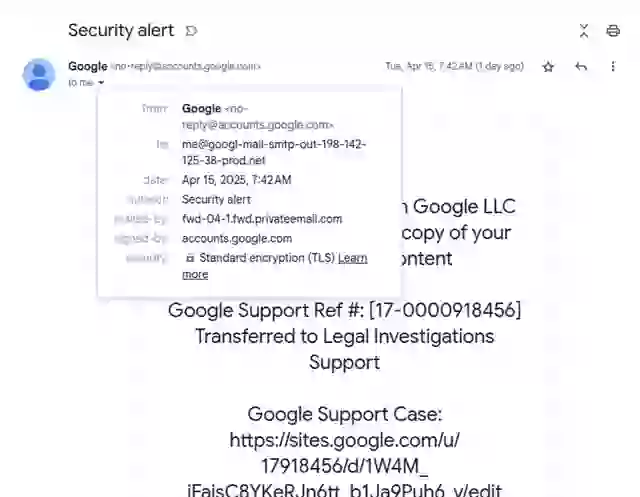
“It really was sent from no-reply@google.com,” Johnson wrote. “It passes the DKIM signature check, and Gmail displays it without any warnings; it even puts it in the same conversation as other legitimate security alerts.”
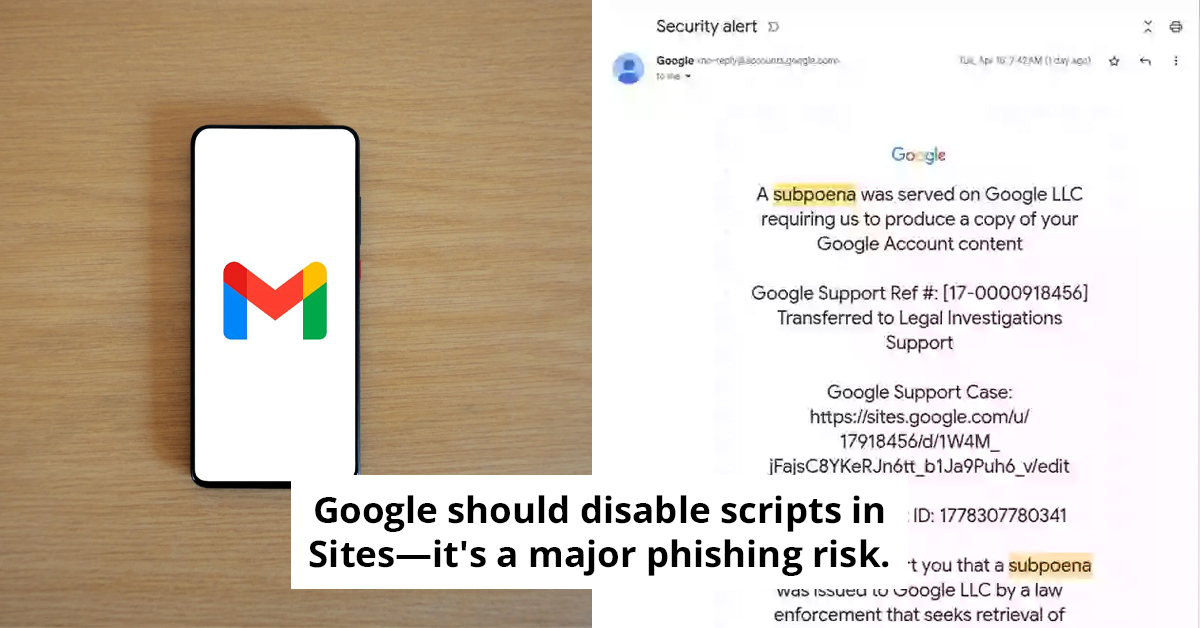
If that sounds dangerous, it’s because it is. The email included a link labeled “Sites,” which opened a page posing as a support portal.
The design? Spot on. The domain? Looked just as official. If you clicked “Upload additional documents” or “View case,” you'd be taken to a login screen that perfectly mimics the real Google sign-in page.
Everything looked right, except for one detail. The page was hosted on sites.google.com, not accounts.google.com.
That small change is your only red flag. Everything else was polished to near perfection, from the email headers to the page layout.
Did you get an email from no-reply@google.com?
So, how do attackers pull off something this slick? According to Johnson, the process is both clever and deeply concerning.
It starts with the scammers registering a domain and setting up a Google account for something like me@domain.com. Next, they create a Google OAuth app, which is usually used to give third-party apps secure access to Google accounts.
But in this case, the scammers use the app to trigger a legitimate Google “Security Alert” email that Google’s system signs and sends itself.
The trick is what happens next: the scammers forward that message to their targets. Because the message is technically still valid, it appears in users’ inboxes without warning signs, often inside threads containing real alerts from Google.
Even the “sent to” field is misleading. Because the attacker named their Google account “me@...,” Gmail displays the recipient as “me,” which is how Gmail typically shortens your address. That subtle touch eliminates another potential tip-off.
 Getty Images
Getty ImagesThe blank space might be a red flag that something’s fishy.
According to Johnson, this phishing campaign relies on two significant gaps in Google’s infrastructure.
First, Google Sites allows users to host content on a Google.com subdomain. There’s no easy way to report abuse directly through the Sites interface, and attackers can quickly change out scripts and embedded content.
Johnson says this alone makes it an ideal staging ground for phishing: “Google should disable scripts and arbitrary embeds in Sites. It’s just too powerful a phishing vector.”But it’s the email’s authenticity that’s the real issue. “The email is much more sophisticated,” Johnson emphasized. The system fails to flag it because of how DKIM works; it checks the message’s headers and content, not the original sending envelope.
 Twitter
Twitter
This email was legitimately sent from no-reply@google.com.
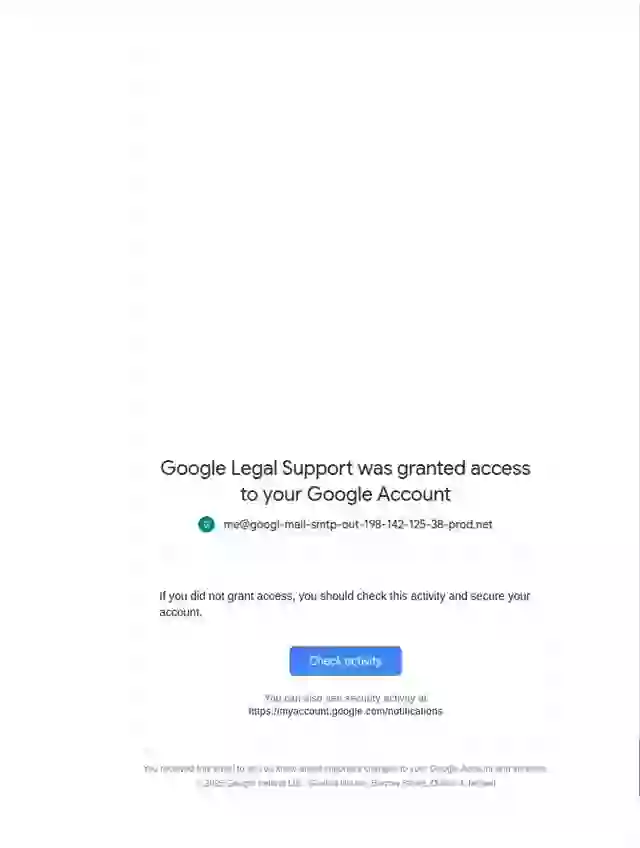
Johnson noticed that while the email appeared to come from Google, it was sent by privateemail.com. Also, buried in a block of space was a second, odd-looking message: “Google Legal Support was granted access to your Google Account.”
That line, paired with the repeated use of the strange me@... address, was another red flag. Johnson reported the issue to Google, which later responded that it plans to fix the OAuth loophole.
 Twitter
Twitter
Understanding Phishing Techniques
Cybersecurity expert Eugene Kaspersky emphasizes that phishing scams have evolved to exploit trust and familiarity. Modern attacks often mimic legitimate communications, using sophisticated designs and personalized messages to trick victims.
He suggests that individuals should verify email headers and URLs before clicking any links. Kaspersky recommends using a multi-layered security approach, including spam filters and antivirus software, to help identify potential threats before they reach the inbox.
Additionally, he advocates for regular education on recognizing phishing attempts as essential for personal and organizational cybersecurity.
Dr. John Gottman, a renowned psychologist known for his work on relationships, points out that strong communication skills can significantly reduce vulnerability to phishing scams. He believes that fostering a culture of open dialogue about digital safety in families and workplaces can empower individuals to recognize suspicious activities.
Moreover, he suggests creating a habit of double-checking sources before taking any action, particularly when financial information is involved. This proactive approach not only enhances personal security but also promotes a supportive environment for discussing online safety.
This phishing email is alarmingly well-crafted.
A Google spokesperson acknowledged the threat, saying:
“We’re aware of this class of targeted attack from this threat actor and have rolled out protections to shut down this avenue for abuse. In the meantime, we encourage users to adopt two-factor authentication and passkeys, which provide strong protection against these kinds of phishing campaigns.”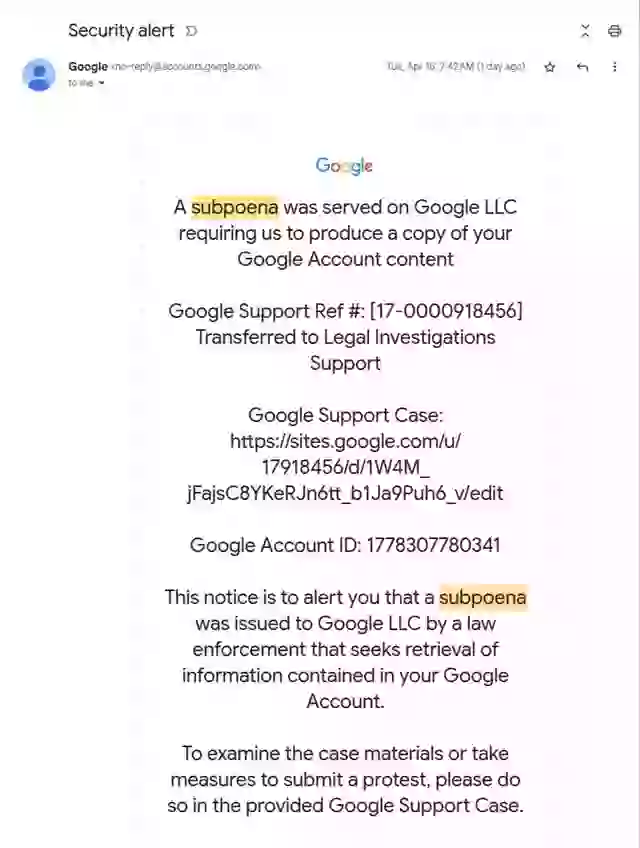 Twitter
Twitter
This attack didn’t rely on technical errors or user laziness. It exploited official systems, appeared in familiar inbox threads, and came from real domains, making it dangerous.
While Google is working on a fix, staying alert is the safest approach right now. Look closely at email addresses, double-check domains, and when in doubt, don’t click. Even a tiny detail can make all the difference.
Healing Approaches & Techniques
As phishing scams continue to evolve, staying informed is crucial for safeguarding personal information. Experts like Kevin Mitnick, a leading cybersecurity consultant, stress the importance of ongoing education about emerging threats. They recommend that individuals and organizations invest in regular training sessions to enhance awareness and preparedness against such attacks.
By adopting a vigilant mindset and implementing practical strategies, such as multi-factor authentication and secure password management, people can significantly reduce their risk of falling victim to these increasingly sophisticated scams. Always remember, a well-informed user is the first line of defense in cybersecurity.




